03 OCT 17
By Morten Andersen
Data which is confidential today will no longer be secure when quantum computers arrive. However, researchers have a solution ready in advance—quantum cryptography.
Banks, intelligence agencies, hospitals, and industrial companies transmit lots of sensitive data in encrypted form. This encryption is generally secure today, but in 20-30 years—when the first computers based on quantum mechanical effects are expected to appear—the situation will be different.
“In other words, today’s encrypted data is essentially being transferred in a non-secure manner,” says Tobias Gehring, Assistant Professor at DTU Physics, noting that the encryption will not be unbreakable in the future.
So what is the answer to invasive quantum computers? Quantum cryptography.
“The necessary protocols have been developed. There could be a product on the market within a few years,” he says.
Secure today is not secure tomorrow
The cornerstone of current encryption is factorization. If you multiply two large primes, it is very difficult for anyone who wants to break the code to work out exactly which two primes lie behind their product. It can be done using a powerful computer, but it takes so long that it is impossible in practice. However, quantum computers will be able to do it quickly.
“The point is that we cannot wait to do something about the problem, even though it lies a few decades in the future. We currently store a lot of data that has to be stored for many years to come. A third party interested in accessing our secrets can electronically intercept the data transfer today and take a copy of the message. While the data is encrypted in a way which is secure now, the interceptor can wait for the quantum computer to be invented and view our data then,” explains Tobias Gehring.
He mentions state secrets as an example. If a foreign power can steal secrets in encrypted form today, it will probably be able to read them long before the country of origin wanted to release them. “There is therefore good reason to quantum encrypt data now, so it cannot be read using a future quantum computer,” argues Tobias Gehring.
Avoid the need for a trusted third party
Part of the solution to the problem is to generate random numbers. This principle is already being used in encryption today, when choosing primes for factorization.
“The classic way of generating random numbers is actually not completely random. In principle, it is possible to predict which numbers will be generated. Using a quantum generator, it will be possible to generate numbers which truly are random,” says Tobias Gehring.
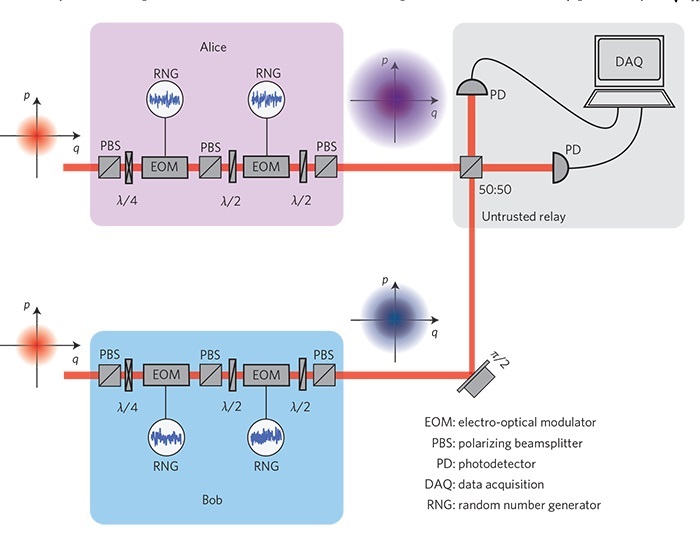
In addition to developing these quantum generators for random numbers, the research group at DTU Physics has made a major breakthrough in the distribution of these random numbers, also called ‘secret keys’.
The technical name for the solution is ‘measurement device independence’, and the research findings were published in the prestigious Nature Photonics journal.
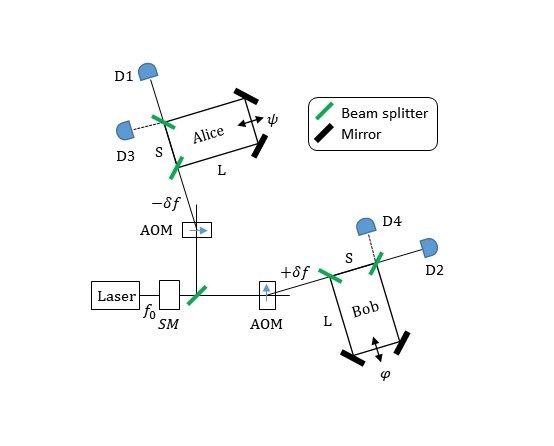
Measurement device independent encryption is different to the usual scenario involving communication between two people, which might be intercepted by a third. Instead, the problem is turned upside down: The two people now communicate only through a third party. They do this by each choosing a secret key, and the third party then receives a mixture of the two secret keys. However, this mixture is not a secret key in itself.
It is actually completely useless unless you know one of the two real secret keys in advance. The third party is responsible for publishing the mixture to the two people who are communicating. Using the information they extract from the mixture, they can calculate the secret key of the other party. This circumvents the uncertainty regarding the third party. The system is designed in such a way that you do not have to trust them. Even if the third party turns out to be a malicious eavesdropper, it does not make the system less secure.
Out of the laboratory and into the market
One major advantage of the solutions the research team has developed is that they do not require new infrastructure. The encrypted information can be exchanged over existing fibre networks.
The task now is to mature the technology so it can move from the laboratories out into the real world.
“We may choose to establish a start-up, but collaborating with existing companies is also an option.”
The road ahead will depend a lot on the market, notes Tobias Gehring:
“We still need to produce some hardware, but that is not the main hold up. The real barrier is that the customers who need to get hold of quantum cryptography have not yet realized that they have a problem.”